Discover Entra.Chat
Entra.Chat

Entra.Chat
Author: Merill Fernando
Subscribed: 13Played: 748Subscribe
Share
© Merill & Joshua Fernando
Description
Entra Chat is a weekly podcast hosted by Merill Fernando and delivers practical insights for Microsoft administrators and security professionals through conversations with identity experts who've been in the trenches.
Episodes feature seasoned Entra practitioners sharing real-world deployment experiences and Microsoft Entra team members who build the features you use daily.
Get the inside track on best practices, implementation strategies, and upcoming capabilities directly from those who design and deploy Microsoft identity solutions.
Join us for actionable takeaways you can apply immediately in your Microsoft 365, Azure, and Entra environments.
---
Entra.Chat, its content and opinions are my (Merill Fernando) own and do not reflect the views of my employer (Microsoft). All postings are provided “AS IS” with no warranties and is not supported by the author. All trademarks and copyrights belong to their owners and are used for identification only.
entra.news
Episodes feature seasoned Entra practitioners sharing real-world deployment experiences and Microsoft Entra team members who build the features you use daily.
Get the inside track on best practices, implementation strategies, and upcoming capabilities directly from those who design and deploy Microsoft identity solutions.
Join us for actionable takeaways you can apply immediately in your Microsoft 365, Azure, and Entra environments.
---
Entra.Chat, its content and opinions are my (Merill Fernando) own and do not reflect the views of my employer (Microsoft). All postings are provided “AS IS” with no warranties and is not supported by the author. All trademarks and copyrights belong to their owners and are used for identification only.
entra.news
41 Episodes
Reverse
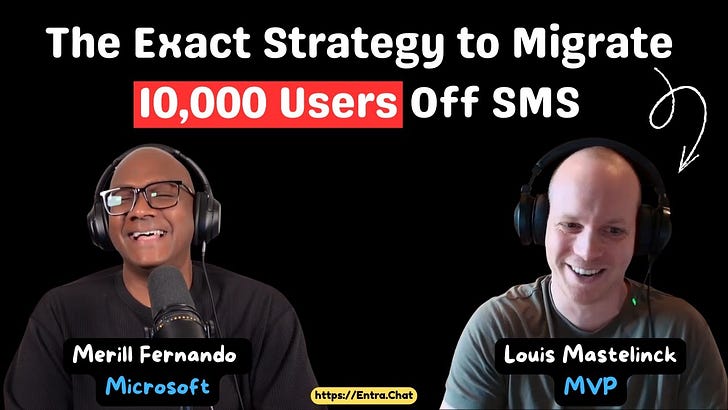
Louis Mastelinck, a Microsoft MVP and Security Consultant at Proximus NXT, joins me to discuss the critical journey of moving organizations away from SMS-based MFA.We deep dive into a practical strategy for migrating users to the Authenticator app, starting with “stopping the bleed” and managing user groups. We also explore a significant security blind spot regarding Email OTP for SharePoint guest access and how to resolve it. Finally, we debate the future of authentication with device-bound versus synced Passkeys and how to defend against downgrade attacks.Subscribe with your favorite podcast player or watch on YouTube 👇About Louis MastelinckLouis Mastelinck is a Security Consultant at Proximus NXT and a recognized Microsoft MVP based in Belgium. Specializing in Incident Response and the full Microsoft Security stack (including MDE, MDO, Sentinel, and Identity Management), he is dedicated to neutralizing threats and securing digital environments. A GCFA-certified professional, Louis is known for his deep technical expertise in areas like Conditional Access and authentication methods.LinkedIn - https://www.linkedin.com/in/louismastelinck/ 🔗 Related Links* Microsoft: Hang up on SMS - http://aka.ms/hangup📗 Chapters00:00 Intro 00:52 Props and PIM 01:41 The Dangers of SMS MFA 04:51 Strategy: Stopping the Bleed 10:06 Migrating Existing Users off SMS 19:20 Impact on Self-Service Password Reset 22:39 The SharePoint Email OTP Security Gap 25:13 Enabling Entra B2B Integration 34:28 Passkeys: Device-Bound vs Synced 44:40 Defending Against MFA Downgrade AttacksPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
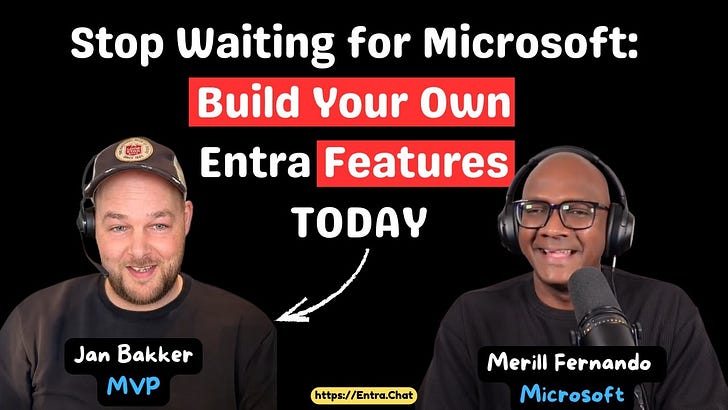
In this week’s episode Jan Bakker, Microsoft MVP and solution architect from the Netherlands, joins us for a masterclass in extending Microsoft Entra ID beyond out-of-the-box capabilities. This episode is your complete guide to building custom identity governance and lifecycle management using Power Apps, Logic Apps, and Azure automation.You’ll learn the fundamental building blocks of automation in the Microsoft ecosystem and how to combine them creatively.Jan’s approach: treat Entra as a platform, not just a product.The automation stack he teaches: → Power Automate (everyday workflows)→ Logic Apps (enterprise automation)→ Dynamic Groups (intelligent triggers)→ Graph API (the foundation of everything)→ Event Hub (cost-effective event streaming)Key topics covered:* Understanding Power Automate vs Azure Logic Apps (and when to use each)* Managed identities and least privilege automation* Dynamic groups as automation triggers* Event Hub for cost-effective event-driven workflows* Custom authentication extensions and token augmentation* Real implementation costs ($50/month for enterprise solutions!)From the conversation:* Step-by-step temporary access pass automation* Automatic refresh token revocation on account disable* MFA method change notifications (like Gmail/Twitter)* Guest lifecycle management and approval flows* Conditional access policy monitoringWhether you’re new to automation or an experienced architect, you’ll walk away with actionable ideas and a new way of thinking about identity solutions.Subscribe with your favorite podcast player or watch on YouTube 👇About Jan BakkerJan is a Microsoft MVP and Solution Architect based in the Netherlands. He is known for his ability to make complex DevOps and Entra concepts accessible and publishes extensive guides on his blog about extending Entra capabilities.LinkedIn: https://www.linkedin.com/in/jan-bakker/🔗 Related Links* Send an email on a new MFA method registration - https://janbakker.tech/send-an-email-on-a-new-azure-mfa-method-registration/* How to build a PowerApp – Temporary Access Pass Manager - https://janbakker.tech/category/power-platform/* Trigger Logic App on group membership changes in Entra ID - https://janbakker.tech/trigger-logic-app-on-group-membership-changes-in-entra-id/* Poor man’s IGA: Monitor and clean up stale guest accounts - https://janbakker.tech/poor-mans-iga-monitor-and-clean-up-stale-guest-accounts/* Poor man’s IGA: Generate Temporary Access Pass for joiners - https://janbakker.tech/poor-mans-iga-generate-temporary-access-pass-for-joiners/* Unlocking the Power of employeeHireDate in Entra ID Dynamic Groups - https://janbakker.tech/unlocking-the-power-of-employeehiredate-in-entra-id-dynamic-groups/* Temporary exclusions for Conditional Access using PIM for Groups - https://janbakker.tech/temporary-exclusions-for-conditional-access-using-pim-for-groups/Sponsored by:Shadow IT and SaaS sprawl are outpacing IT teamsIt can feel impossible to tackle these app governance challenges:📦 Entra ID isn’t secure by default💥 SaaS adoption & sprawl isn’t slowing down⌨️ Citizen Development keeps rising (hello, Copilot Studio!)🗑️ Vendors often don’t remove apps after uninstall🔃 Offboarding is inconsistent or doesn’t happen at all🥔 App governance is passed around like a hot potatoENow AppGov Score shines a light on lurking risks, providing a free App Governance Benchmark Report for your Entra tenant. Reclaim control and protect against breach & disruptions. Free upgrade to Standard Tier for 7 days once you get your score.Secure & Govern Entra Apps Now📗 Chapters00:03 The Poor Man’s IGA Concept 00:07 Revoking Refresh Tokens Automatically 00:13 Power Apps for Approval Workflows 00:16 Custom Logic for Managing Guest Access 00:19 Building a Temporary Access Pass Tool 00:25 Power Automate vs. Azure Logic Apps 00:28 Triggering Automation with Event Hubs 00:31 Alerting on Security Changes via Audit Logs 00:41 Self-Service Group Management 00:44 Why You Must Learn Graph APIPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
Khurram, a key member of the internal App Governance assessment team at Microsoft, joins the show to pull back the curtain on how Microsoft manages application security at a massive corporate scale and the rigorous internal security measures Microsoft employs to protect its corporate Entra ID tenant from risky applications.In this deep dive, Khurram reveals Microsoft’s custom-built App Governance blueprint. He details the process for reviewing and consenting to the hundreds of new application requests the organization receives monthly.Key Takeaways* Permission Risk Rating: Learn how Microsoft’s team assesses and assigns a severity rating—Low, Moderate, Important, or Critical—to permissions. This rating is based on the permission’s capability, whether it’s delegated or application, and its potential for PII exposure (e.g., Application permission or a .all scope will score higher).* The Weighting Model: Discover how the Microsoft app assessment team has proactively risk-rated between 3,000 and 3,500 permissions. This approach dictates when an app is automatically approved (for low-risk requests like User.Read) versus when it is flagged for manual, scenario-based review.* Holistic Risk Review: Khurram explains how the app’s overall risk is calculated beyond just permissions. This includes mandatory security controls like banning high-risk reply URLs (e.g., azurewebsites.net and aka.ms) , enforcing the use of certificates over secrets , and requiring multiple owners.* Multi-Team Veto Power: Understand the critical approval workflow where requests for higher-risk permissions are routed to specific organizational data owners (like the DLP, Identity, or Exchange teams). All teams must approve the request as a whole, giving each team a critical veto power over access to their services.Subscribe with your favorite podcast player or watch on YouTube 👇About Khurram ChaudharyKhurram is a Principal Security Assurance Eng on the internal assessment team at Microsoft. He specializes in App Governance and was instrumental in developing the systems and risk-rating methodologies used to manage thousands of application requests within Microsoft’s corporate tenant.🔗 Related Links* Entra Application Management - https://learn.microsoft.com/en-us/entra/identity/enterprise-appsSponsored by:Shadow IT and SaaS sprawl are outpacing IT teamsIt can feel impossible to tackle these app governance challenges:📦 Entra ID isn’t secure by default💥 SaaS adoption & sprawl isn’t slowing down⌨️ Citizen Development keeps rising (hello, Copilot Studio!)🗑️ Vendors often don’t remove apps after uninstall🔃 Offboarding is inconsistent or doesn’t happen at all🥔 App governance is passed around like a hot potatoENow AppGov Score shines a light on lurking risks, providing a free App Governance Benchmark Report for your Entra tenant. Reclaim control and protect against breach & disruptions. Free upgrade to Standard Tier for 7 days once you get your score.Secure & Govern Entra Apps Now📗 Chapters01:21 The Shift to Admin Consent 03:38 Factors for Reviewing App Risk 06:35 How We Rate Permission Severity 09:25 Automating Low-Risk Approvals 14:17 The Internal Review Workflow 21:40 The App Governance Scoring System 29:01 The Localhost Redirect Debate 39:35 Handling Stale Apps and Permissions 49:34 Advice for Identity AdminsPodcast Apps🎙️ Entra.Chat → https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
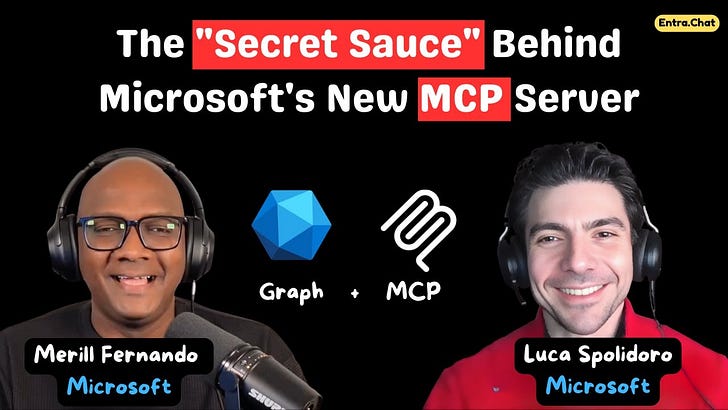
Luca Spolidoro from the Microsoft Entra AI Innovations team joins us to unveil the new Microsoft MCP Server for Enterprise. We discuss how this innovation allows admins and AI agents to interface with their tenant using natural language, bridging the gap between LLMs and the complexity of Microsoft Graph.We also talk about the technical challenges of token limits, the patented “three-tool” solution that optimizes queries, and the roadmap for write operations and PowerShell script generation.Subscribe with your favorite podcast player or watch on YouTube 👇About Luca Spolidoro Luca is a Product Manager on the Entra AI Innovations team at Microsoft. Formerly working on advanced queries for Microsoft Graph, he now focuses on enabling AI agents to interact securely and efficiently with directory objects and tenant data. LinkedIn - https://www.linkedin.com/in/lucaspolidoro/🔗 Related Links * Microsoft MCP Server for Enterprise - https://aka.ms/mcp/entraSponsored by:Shadow IT and SaaS sprawl are outpacing IT teamsIt can feel impossible to tackle these app governance challenges:📦 Entra ID isn’t secure by default💥 SaaS adoption & sprawl isn’t slowing down⌨️ Citizen Development keeps rising (hello, Copilot Studio!)🗑️ Vendors often don’t remove apps after uninstall🔃 Offboarding is inconsistent or doesn’t happen at all🥔 App governance is passed around like a hot potatoENow AppGov Score shines a light on lurking risks, providing a free App Governance Benchmark Report for your Entra tenant. Reclaim control and protect against breach & disruptions. Free upgrade to Standard Tier for 7 days once you get your score.Secure & Govern Entra Apps Now📗 Chapters 03:36 The Hackathon Origin Story 05:55 What is the Model Context Protocol? 09:22 The Token Limit Problem 15:45 Microsoft’s “Secret Sauce” Solution 19:54 Current Limitations & Future Scope 23:57 Future: Write Operations & Scripts 30:12 Security & Admin Controls 42:43 Security Copilot vs. Standalone MCP 50:21 Getting StartedPodcast Apps 🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple 📺 YouTube → https://entra.chat/youtube 📺 Spotify → https://entra.chat/spotify 🎧 Overcast → https://entra.chat/overcast 🎧 Pocketcast → https://entra.chat/pocketcast 🎧 Others → https://entra.chat/rssMerill’s socials 📺 YouTube → youtube.com/@merillx 👔 LinkedIn → linkedin.com/in/merill 🐤 Twitter → twitter.com/merill 🕺 TikTok → tiktok.com/@merillf 🦋 Bluesky → bsky.app/profile/merill.net 🐘 Mastodon → infosec.exchange/@merill 🧵 Threads → threads.net/@merillf 🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
This week, I’m joined by a stellar panel of Nathan McNulty, Ru Campbell, Martin Sandren, and Thomas Naunheim to break down the firehose of news from Microsoft Ignite related to Entra. We dive straight into the hot debate over synced passkeys versus device-bound credentials and why consumer adoption might force our hand in the enterprise. We also explore the new Account Recovery features that could save companies thousands in helpdesk costs and unpack the massive shift toward “Agentic AI” with the launch of Entra Agent ID, a feature that fundamentally changes how we think about non-human identities. If you are feeling overwhelmed by the pace of AI and identity changes, you are not alone. Listen in as we figure this out together.Subscribe with your favorite podcast player or watch on YouTube 👇About our guests* Nathan McNulty: Nathan is a Senior Security Solutions Architect at Patriot Consulting and a Microsoft Security MVP. He has been working with Microsoft cloud identity solutions since the days of Live@edu and Office 365 in 2010.* https://www.linkedin.com/in/nathanmcnulty/* Ru Campbell: Ru is a Microsoft Security MVP who leads Microsoft Security at Threatscape. He describes himself as a “jack of all trades” when it comes to Microsoft 365 security, getting involved in a wide range of security topics.* https://www.linkedin.com/in/rlcam/* Martin Sandren: Martin is the Product Lead for Identity Access at Inter IKEA, where he manages identity solutions across the globe. He offers a unique perspective as a practitioner running identity for a massive enterprise.* https://www.linkedin.com/in/martinsandren/* Thomas Naunheim: Thomas is a Cloud Security Architect at glueckkanja and a Microsoft Security MVP. He specializes in cloud security architecture and actively tracks new features and announcements in the Microsoft ecosystem.Sponsored by:Shadow IT and SaaS sprawl are outpacing IT teamsIt can feel impossible to tackle these app governance challenges:📦 Entra ID isn’t secure by default💥 SaaS adoption & sprawl isn’t slowing down⌨️ Citizen Development keeps rising (hello, Copilot Studio!)🗑️ Vendors often don’t remove apps after uninstall🔃 Offboarding is inconsistent or doesn’t happen at all🥔 App governance is passed around like a hot potatoENow AppGov Score shines a light on lurking risks, providing a free App Governance Benchmark Report for your Entra tenant. Reclaim control and protect against breach & disruptions. Free upgrade to Standard Tier for 7 days once you get your score.🔗 Related Links* Microsoft Entra: What’s New in Secure Access on the AI Frontier* Entra.Chat - Access Review Agent* Entra.Chat - Conditional Access Agent📗 Chapters00:00 Intro04:36 The Debate: Synced vs Device-Bound Passkeys20:47 Entra Account Recovery & Identity Verification30:00 Passwordless Self-Remediation33:01 Security Copilot Comes to E536:47 The Rise of AI Agents in Entra42:49 Understanding Entra Agent ID56:47 MCP Servers & VS Code Integration01:05:20 Global Secure Access & AI Security01:09:14 Microsoft Security BaselinePodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
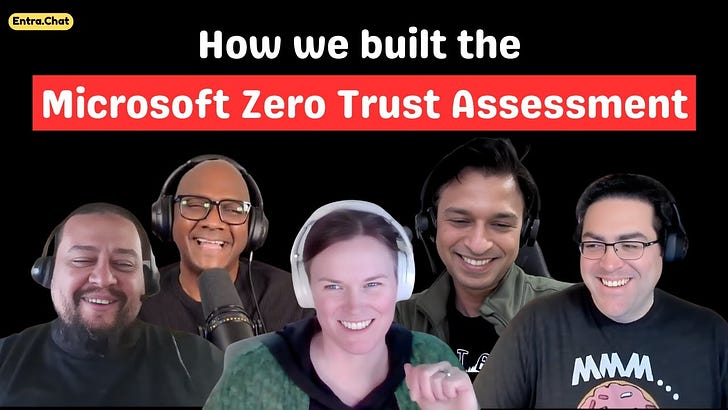
This week, I’m so excited to share the inside story of a project I’ve been working on for over a year: the new Zero Trust assessment. I’m joined by some of the key folks from the team: Tarek, who’s leading the charge; Sarah and John, who are crushing docs; and Ravi, who’s owning Intune.We unpack the wild breach that sparked it all, geek out over those Sankey charts that spotlight sneaky unmanaged devices and privileged access landmines, and tease why even “expired” app creds could be your silent killer. If you’re tired of silos between identity and endpoints, this is your wake-up call—tune in to see how to make Zero Trust practical before the next attack hits.Subscribe with your favorite podcast player or watch on YouTube 👇About Our GuestsSarah LipseySarah Lipsey has been with Microsoft for almost four years and writes about monitoring and health, ID Protection, and Security Copilot in Microsoft Entra. Sarah has worked as a technical writer and instructional designer for around 20 years, and for a university, a telecommunications firm, and a railroad. She lives in the woods with her family where she loves to knit, play video games, hike, and ski. Yes, she spends way too much time trying to close out every dot on a video game map. Still working on the Skellige map for The Witcher 3.LinkedIn - https://www.linkedin.com/in/sarah-lipsey-b53b746/John FloresJohn is a Senior Content Developer at Microsoft, where he has worked for over eight years. He specializes in creating high-impact technical content for identity security within Microsoft Entra, focusing on areas like Conditional Access, MFA, ID Protection, and device identity. John also leads the documentation efforts for Zero Trust content across Microsoft 365 and Identity teams. He actively collaborates with engineers and PMs to test pre-release features and engages with customers to refine technical guidance.LinkedIn - https://www.linkedin.com/in/johnbflores/Ravi KalwaniRavi is a Senior Program Manager at Microsoft, based in Sydney, Australia. With over 14 years of IT experience spanning technical training, support, consulting, and program management, his focus for the past five years has been on Enterprise Client and Mobility, specifically Microsoft Configuration Manager and Intune. Ravi is also an experienced public speaker, having presented at numerous technical conferences and delivered a wide range of workshops for both internal teams and enterprise customers.LinkedIn - https://www.linkedin.com/in/rkalwani/Tarek DawoudTarek Dawoud is a long-time veteran at Microsoft, having been with the company for over 18 years. Tarek currently leads the architecture team within the customer engineering (CXE) organization, where he helps customers deploy Entra, gathers insights for the product group, and works to solve the hardest identity problems.LinkedIn - https://www.linkedin.com/in/tarekdawoud/🔗 Related Links* aka.ms/zerotrust/assessment → Microsoft Learn docs page for the assessment* aka.ms/zerotrust/demo → Interactive demo of a sample assessment report* aka.ms/zerotrust/feedback → Share your feedback* aka.ms/zerotrust/issues → Logging bugs & issuesZero Trust Assessment - Five minute walkthroughZero Trust Assessment ReportSample report generated by the Zero Trust Assessment tool. Try aka.ms/zerotrust/demo for an interactive demo.📗 Chapters00:00 Intro 01:11 The Origin Story: A Customer Breach 05:59 A New Way to Write Docs 08:55 Bringing Intune into the Story 11:07 How This Compares to Secure Score 14:46 Uncovering Insights with Sankey Charts 21:55 Behind the Scenes: How a Test is Built 36:18 Why We Target Privileged Access (AI Attackers) 39:59 The Myth of “Safe” Expired Credentials 42:35 Final Thoughts: “Please Run It”Podcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode, I sit down with security researcher Katie Knowles to unpack the hidden layers of identity systems inside Microsoft Entra. We get into real-world attack paths like backdooring service principals, restricted administrative units that can accidentally create unstoppable accounts, and OAuth phishing in Copilot Studio. Katie also shares how she approaches deep technical research, what defenders often overlook, and why identity security is only becoming more complex. This is one of those conversations where you walk away thinking differently.Subscribe with your favorite podcast player or watch on YouTube 👇About Katie KnowlesKatie Knowles is a Senior Security Researcher at Datadog specializing in Microsoft Azure and Entra ID security. She has extensive experience across security engineering, penetration testing, and incident response. Katie is known for her thorough research that connects complex technical vulnerabilities to practical defensive guidance, publishing regularly on Datadog Security Labs and speaking at major security conferences.LinkedIn - https://www.linkedin.com/in/kaknowles/🔗 Related Links* Katie’s Datadog security posts - https://securitylabs.datadoghq.com/articles/?author=Katie_Knowles* Katie’s personal blog - https://kknowl.es* Katie’s conference talks - https://kknowl.es/external-content/* Creating immutable users through a bug in Entra ID restricted administrative units - https://securitylabs.datadoghq.com/articles/creating-immutable-users-entra-id-administrative-units/* I SPy: Escalating to Entra ID’s Global Admin with a first-party app - https://securitylabs.datadoghq.com/articles/i-spy-escalating-to-entra-id-global-admin/* CoPhish: Using Microsoft Copilot Studio as a wrapper for OAuth phishing - https://securitylabs.datadoghq.com/articles/cophish-using-microsoft-copilot-studio-as-a-wrapper/📗 Chapters02:08 The Immortal User Bug in Restricted Admin Units04:23 Attacker Impact: The Un-deletable Malicious Account05:59 Hacking First-Party Apps & Bypassing AppLock09:29 How She Found the AppLock Bypass11:16 A Day in the Life of a Security Researcher14:20 Phishing with Copilot Studio & OAuth17:00 Top Tips for App Governance & Security21:45 The Hidden Risk of Azure Key Vault Access Policies28:55 App Registrations vs. Service Principals Explained41:48 The Future: Agent IDs & The New Trust ModelPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
Sami Lamppu and Thomas Naunheim, the creators of the Entra ID Attack and Defense Playbook, join me to discuss their incredible 5-year community project.We talk about the most complex attacks they’ve researched, including the “black box” token and PRT attacks, and their shocking findings related to TPM and device compliance. We also dive deep into their brand-new chapter on the new Microsoft Entra Connect Application Based Authentication model and the critical steps you must take to secure it.Subscribe with your favorite podcast player or watch on YouTube 👇About Sami & ThomasSami Lamppu is a Microsoft Security MVP and a Principal Cloud Security Lead at Elisa with a strong focus on the blue team side, helping organizations proactively prevent attacks.Thomas Naunheim is a Cybersecurity Architect at glueckkanja and a Microsoft Security MVP. He specializes in Microsoft Entra, identity and access management, and cloud security posture.* Sami LinkedIn - https://www.linkedin.com/in/sami-lamppu/* Thomas LinkedIn - https://www.linkedin.com/in/thomasnaunheim/🔗 Related Links* Entra ID Attack and Defense Playbook - https://github.com/Cloud-Architekt/AzureAD-Attack-Defense📗 Chapters02:35 Origin Story of the Playbook 07:08 Overview of the Attack Chapters 09:53 Who is the Playbook For? 13:59 The Hardest Chapter to Write: Tokens 21:48 Shocking PRT & TPM Findings 24:43 NEW Chapter: Hacking Entra Connect (ABA) 29:10 How to Secure the New Sync Account 36:53 HSCAR: The Posture Analyzer Tool 45:09 Keeping the Playbook Updated & Community 53:12 What’s Next & Final AdvicePodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode, I chat with Dirk-jan Mollema, the legendary researcher behind some of the most important discoveries in Microsoft identity security. We go deep into how curiosity led him from tinkering with web tools to uncovering one of the biggest Entra ID vulnerabilities ever found. He shares the story behind the CVE that rocked the cloud world, the stress of realizing what he’d uncovered, and the mindset that drives his relentless research. If you’ve ever wondered what it feels like to find a bug that could break the internet—this one’s for you.PS: If you like this episode please leave a review on Apple Podcast or Spotify 🙏Subscribe with your favorite podcast player or watch on YouTube 👇About Dirk-jan MollemaDirk-Jan Mollema is a security researcher and consultant specializing in Microsoft Entra ID (Azure AD) and Active Directory security. He is the creator of popular offensive security tools including ROADtools and ROADrecon. With seven years of Entra research and nearly a decade in AD security, Dirk-Jan has discovered numerous critical vulnerabilities and has played an important role in helping improve Microsoft’s cloud security posture. He provides training and consulting services through his company Outsider Security.Twitter → https://twitter.com/_dirkjanLinkedIn → https://www.linkedin.com/in/dirkjanmContact → https://outsidersecurity.nl🔗 Related Links* One Token to rule them all - obtaining Global Admin in every Entra ID tenant via Actor tokens - https://dirkjanm.io/obtaining-global-admin-in-every-entra-id-tenant-with-actor-tokens* Dirk-Jan’s Blog - https://dirkjanm.io* ROADtools - https://github.com/dirkjanm/ROADtools📗 Chapters00:00 Intro02:11 Guest Journey into Security07:13 Building ROADtools and ROADrecon09:53 Research Tools & Methods14:05 Top Discoveries Ranked17:01 Windows Hello & PRT Deep Dive26:07 The Cross-Tenant Actor Token Bug35:34 Ethical Dilemmas of Big Finds38:24 Disclosure, Impact & Community45:59 Future Research & Intune Tips53:58 Training, Consulting & ClosingPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode, I sit down with Alexander Filipin, a Product Manager at Microsoft, to unpack the essentials of identity governance and why access reviews are a game-changer for security and compliance.We explore the pitfalls like rubber stamping that plague traditional methods and tease how the new AI-driven Access Review Agent is stepping in with smart recommendations and context to make decisions easier and more accurate. Plus, we peek into exciting future possibilities where agents could automate access management entirely—tune in to see how this could reshape your org’s approach!Subscribe with your favorite podcast player or watch on YouTube 👇About Alexander FilipinAlexander Filipin is a Product Manager at Microsoft in the Microsoft Entra ID Governance team. With a background in consulting and identity security, he previously contributed to popular community projects like Conditional Access as Code and now leads features in Microsoft Entra, including the newly released Access Review Agent.LinkedIn - https://www.linkedin.com/in/alexfilipin/🔗 Related Links* Microsoft Entra Access Review Agent Documentation - https://aka.ms/aragent* Conditional Access Optimization Agent - https://learn.microsoft.com/en-us/entra/identity/conditional-access/agent-optimization📗 Chapters00:00 Intro00:48 From Community Code to Microsoft Product Management04:42 The 4 Drivers of Governance: Security, Compliance, & Cost Savings06:45 Why Access Reviews are Critical for Guest and Licensing Cleanup13:46 Licensing: Entra ID P2 vs. Entra Governance Capabilities20:01 The Biggest Problem with Traditional Access Reviews Today20:41 Introducing the Entra Access Review Agent23:18 The Role of AI in Generating Reviewer Context34:04 The Audit Trail and Compliance for AI Decisions44:26 Future Vision: The Next Evolution of Identity GovernancePodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
Welcome back to Entra.Chat! In this rapid-fire Q&A, I’m joined by a team of brilliant CXE Identity Architects from Microsoft, and they’re answering the toughest questions on the future of identity. We dive deep into the security challenge posed by agentic AI that can spawn self-replicating identities and how Microsoft is creating tailored behavioral analytics to protect your environment. The team also spills the details on the shift to phishing-resistant MFA through authentication strengths capabilities for Entra ID tenants—you’ll definitely want to listen before your next audit!Subscribe with your favorite podcast player or watch on YouTube 👇About The PanelThis episode features an incredible panel of experts from Microsoft’s Identity team:* Tarek Dawoud: Lead Architect of the Architecture Team, focusing on AI for Security and Entra Resilience → https://www.linkedin.com/in/tarekdawoud/* Tyler Chan: Architect focusing on the Zero Trust Workshop and the healthcare vertical → https://www.linkedin.com/in/chantylert/* Ramiro Calderon: Architect on the team focusing on Identity and Access Management and helping customers move to the cloud → https://www.linkedin.com/in/ramirocalderon/* Jas Suri: Architect for Customer Identity and Access Management (CIAM), including Entra External ID as well as passwordless technologies → https://www.linkedin.com/in/jas-suri-aa644a7b/* Ehud Itshaki: Identity Architect focusing on AI’s impact on identity systems and government customers → https://www.linkedin.com/in/ehudi/* Thomas Detzner: Architect focusing on Global Secure Access (GSA) and the network pillar of Zero Trust. → https://www.linkedin.com/in/thomasdetzner/* Travis Gross: Manager and lead of the overall Identity CxE team at Microsoft → https://www.linkedin.com/in/travis-gross-536b3b9b/* Keith Brewer: Architect for Entra authentication, identity security, and U.S. government customers → https://www.linkedin.com/in/keith-b-145519174/🔗 Related Links* The future of AI agents—and why OAuth must evolve - https://techcommunity.microsoft.com/blog/microsoft-entra-blog/the-future-of-ai-agents%E2%80%94and-why-oauth-must-evolve/3827391* Beyond OAuth: Why SCIM must evolve for the AI agent revolution - https://techcommunity.microsoft.com/blog/microsoft-entra-blog/beyond-oauth-why-scim-must-evolve-for-the-ai-agent-revolution/4433036* Use Kerberos for single sign-on (SSO) to your resources with Microsoft Entra Private Access - https://learn.microsoft.com/en-us/entra/global-secure-access/how-to-configure-kerberos-sso* Bulk operations in Microsoft Entra ID (Preview) - https://learn.microsoft.com/en-us/entra/fundamentals/bulk-operations* Road to the cloud: AD to Entra ID - aka.ms/AD2AAD* Microsoft Entra security operations guide - Incident Response Playbooks - https://learn.microsoft.com/en-us/entra/architecture/security-operations-introduction* Incident response playbooks - https://learn.microsoft.com/en-us/security/operations/incident-response-playbooks* Review permissions granted to enterprise applications - https://learn.microsoft.com/en-us/entra/identity/enterprise-apps/manage-application-permissions?pivots=portal* Multi-factor unlock - https://learn.microsoft.com/en-us/windows/security/identity-protection/hello-for-business/multifactor-unlock?tabs=intune* API-driven Inbound Provisioning - Integration scenarios - https://learn.microsoft.com/en-au/entra/identity/app-provisioning/inbound-provisioning-api-logic-apps#integration-scenario-variations📗 Chapters03:57 The Challenge of Agentic AI and Identity 06:35 Top Identity Security Enhancements You Can Use Today 09:42 Entra External ID: Syncing Tenants and B2C Migration 11:41 Restoring Compromised Tenants15:01 Verifying Real Humans: Identity Assurance Levels (IAL) Explained 17:01 Rethinking App Consent and Granular Admin Roles 18:28 Clearing Up Confusion: Passkeys vs Phishing-Resistant MFA 20:33 Ditching On-Prem: Moving Legacy Apps with Private Access 23:14 How AI Will Change IAM Admins & Permissions Forever 30:31 Is Entra ID Governance the End of MIM?Podcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode, I sit down with my longtime friends and colleagues, Jas Suri and Gayan Randeny, at Microsoft’s campus to unpack the biggest Microsoft consumer identity shift in years—Azure AD B2C’s sunset and the rise of Entra External ID. We talk about why B2C is going away, the crazy scale of tenants with 100M+ identities, the migration paths and what the future looks like for customer identity. Plus, stick around until the end because Gayan and Jas share a world premiere on the podcast about a groundbreaking new Just-In-Time migration approach that will make moving millions of users to Entra External ID simpler than you think. You don’t want to miss this scoop!If you want to stay ahead of this massive transition, this is a must-listen.Subscribe with your favorite podcast player or watch on YouTube 👇About Jas SuriJas Suri is the CxE Architect PM for Microsoft Entra External ID and has a wealth of knowledge and experience in helping Microsoft customers deploy Azure AD B2C and Entra External ID. With extensive experience in Azure AD B2C and Entra External ID migrations, Jas has now taken on the CxE architect role for passkeys across both Entra ID and Entra External ID..LinkedIn - https://www.linkedin.com/in/jas-suri-aa644a7b/About Gayan RandenyGayan Randeny is a seasoned expert in customer identity and access management at Microsoft, with years of experience helping customers deploy Azure AD B2C and now leading efforts to migrate to Entra External ID. In addition to his work on Entra External ID, Gayan is now turning his attention to help enterprise customers deploy Global Secure Access.LinkedIn - https://linkedin.com/in/gyanrandhani🔗 Related Links* Migrating users to Microsoft Entra External ID - https://learn.microsoft.com/en-us/entra/external-id/customers/how-to-migrate-users* Microsoft Entra External ID deployment architectures with Microsoft Entra - https://learn.microsoft.com/en-us/entra/architecture/external-identity-deployment-architectures* Azure Active Directory B2C: Custom CIAM User Journeys - https://github.com/azure-ad-b2c/samples📗 Chapters00:00 Intro00:57 What is B2C and why it mattered03:44 The insane scale of B2C (100M+ identities)05:02 Why B2C is going away07:20 Converging enterprise and customer identity12:01 Migration differences: B2C vs Entra External ID18:24 Just-in-time and passwordless migration23:09 Hybrid tenant approach explained29:15 Migration strategies and best practices33:29 New features, partners, and what’s next36:44 Closing thoughtsPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
On this episode of Entra Chat, I was thrilled to sit down with Yanyan and Sweta from the Entra UI experience team to dive deep into a feature that many of us have used but is now getting a massive refresh: Bulk Operations. We talked about how they took a critical legacy tool and completely re-engineered it for insane performance and scale, making it more reliable than ever. You’ll hear about some amazing new capabilities, like customizing the columns in your CSV exports and using UPNs instead of just Object IDs to add users, which is a huge time-saver. We even get a behind-the-scenes look at the engineering that makes it possible to export over a million groups in just 10 minutes!Subscribe with your favorite podcast player or watch on YouTube 👇About Yanyan JuYanyan Ju is a Principal Engineer Manager at Microsoft, where she is dedicated to delivering the best administrative experience for Microsoft customers. She focuses on creating value through user-friendly and consistent admin interfaces, shaping the future of AI-powered Entra Admin UX, and leading as part of a UX Engineering Center of Excellence.* LinkedIn: https://www.linkedin.com/in/yanyan-ju-194545239/About Sweta KumariSweta Kumari is a Product Manager at Microsoft, focusing on identity and access management within Microsoft Entra. Sweta leads initiatives around Entra Admin feature enhancements, Customer feedback integration and Privileged Identity Management (PIM). Her work emphasizes improving user experience, and ensuring secure, compliant access for customers.* LinkedIn: https://www.linkedin.com/in/sweta-kumari-557478127/🔗 Related Links* Bulk operations in Microsoft Entra ID (Preview) - https://learn.microsoft.com/en-us/entra/fundamentals/bulk-operations📗 Chapters00:01:20 What is Bulk Operations? 00:03:40 Supported Bulk Operations 00:06:34 Customizing Your Exports 00:08:45 How is it different from PowerShell? 00:11:29 Adding Members in Bulk (The Easy Way) 00:13:56 Bulk Deleting Safely 00:16:12 Why Was The Feature Rebuilt? 00:19:05 The Engineering Overhaul 00:23:02 Insane Performance Gains 00:25:19 How to Share Your FeedbackPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill’s socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
Cybersecurity expert Erica shares her incredible journey from pharmacist to becoming a professional hacker. She reveals how attackers are bypassing modern security controls like MFA and what you can do to protect your tenant.We talk about the most common configuration vulnerabilities that exist in almost every organization, the dangers of application onboarding, and the top five phishing vectors threat actors are using to gain initial access, including clever abuses of Microsoft Teams.Subscribe with your favorite podcast player or watch on YouTube 👇About EricaErica has an amazing career arc, starting in pharmacy before pivoting to cybersecurity. With a deep, hands-on understanding of offensive security gained from platforms like Hack the Box and real-world penetration testing, she specializes in protecting and defending Microsoft Cloud tenants. Erica is passionate about sharing her knowledge on how to better protect your tenant and what bad guys are looking for.LinkedIn - https://www.linkedin.com/in/erica-z-b4169598/🔗 Related Links* Blog - https://ericazelic.medium.com/* Hack The Box - https://www.hackthebox.com/* Altered Security - https://www.alteredsecurity.com/📗 Chapters00:00:00 Intro 00:02:14 From Pharmacy to Cybersecurity 00:07:19 Learning to Hack with Hack The Box 00:11:45 The First Cloud Hack: M365 Public Groups 00:17:50 The Hidden Dangers of App Onboarding 00:25:53 The 5 Modern Phishing Attack Vectors 00:30:36 Bypassing MFA with Device Code Phishing 00:34:34 Adversary-in-the-Middle & Auth Downgrade Attacks 00:48:24 The Secret to Mastering Cybersecurity SkillsPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
Jeremy Conley, Product Manager on the Identity Governance team at Microsoft, demystifies the world of guest access in Microsoft Entra. We discuss the hidden security risks that accumulate as guests are invited into a tenant and the governance challenges this creates.We also do a deep dive into the different licensing tiers, from P2 to the new Entra ID Governance for Guests license, and explain the recently GA’d , cost-effective MAU-based billing model for guests. Jeremy provides actionable tips for admins to start cleaning up their tenants and implementing a robust governance strategy today.Subscribe with your favorite podcast player or watch on YouTube 👇About Jeremy ConleyJeremy Conley is a Product Manager at Microsoft, focusing on identity governance. His work is centered on Entitlement Management and the governance of guest and external users within Microsoft Entra, helping customers secure their environments and manage user lifecycles effectively.LinkedIn - https://www.linkedin.com/in/jeremy-conley-99552379/🔗 Related Links* Microsoft Entra ID Governance licensing for guest users • aka.ms/EntraIDGuestGovernance* PowerShell tool to update guest sponsor info • Update-MsIdInvitedUserSponsorsFromInvitedBy📗 Chapters00:51 What are Guests & External Users? 03:51 The Hidden Security Risk of Guests 07:14 Understanding Licensing for Guest Governance 09:10 P2 Features: Entitlement Management & Access Reviews 15:19 Entra ID Governance: Lifecycle Workflows & Automation 20:33 The "Sponsor" Concept for Guest Accountability 25:49 The NEW Guest Licensing Model Explained28:15 Demystifying the 1:5 Ratio vs. MAU Billing35:18 Common Mistakes Admins Make with Guests 37:22 A Simple First Step to Clean Up Your TenantPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode of Entra.Chat, I dive into the critical world of app governance with experts Jay Gundotra and Sander Berkouwer, who unpack the hidden risks of non-human identities in Microsoft Entra. From shocking real-world breaches like Midnight Blizzard to a hilarious tale of a theme park’s water supply mishap, we explore why securing your cloud apps is more urgent than ever. Tune in to discover practical tips and tools to safeguard your organization without losing your giraffes!Subscribe with your favorite podcast player or watch on YouTube 👇About Jay GundotraJay is the CEO and technical founder of E-Now. He has a long history as an Exchange and Active Directory engineer, which led him to found his company and focus on solving complex identity and application governance challenges for enterprises.LinkedIn - https://www.linkedin.com/in/jay-gundotra-19079a/About Sander BerkouwerSander Berkouwer is a 17-year Microsoft MVP veteran and an accomplished identity architect. With deep expertise from being "in the trenches," he partners with Jay to educate the community and build solutions for managing non-human identities and service principals.LinkedIn - https://www.linkedin.com/in/sanderberkouwer/🔗 Related Links* AppGov Community - https://community.appgovscore.com/* How Ownerless Apps in Entra ID Increase Your Attack Surface* Securing Workload Identities in Entra ID: A Practical Guide for IT and Security Teams📗 Chapters00:00 Intro 01:55 What is App Governance? 04:02 The Origin Story of Focusing on App Governance 08:35 Why App Security is Critical Today 14:15 The Dangers of Over-Privileged Apps 20:38 The Giraffe Story: When Cleanup Goes Wrong 24:42 What Should a Successful Organization Do? 30:22 The Full Application Lifecycle: Onboarding to Offboarding 35:38 Building the AppGov Community 45:04 The Importance of Education and AutomationPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode of Entra.Chat, I dive deep with cybersecurity architect Fabian Bader into his research on bypassing poorly designed Microsoft Entra’s conditional access policies and what you can do about them. We also cover the game-changing new Group Source of Authority feature that lets you finally manage synced groups in the cloud, and share insights from Fabian’s work with MSRC to secure the platform—don’t miss this one if you want to stay ahead in cloud security!Subscribe with your favorite podcast player or watch on YouTube 👇About Fabian BaderFabian Bader is a Cybersecurity Architect at glueckkanja, based in Hamburg, Germany. He is a well-known researcher in the Microsoft identity space, creator of the Cloud Brothers blog, and creator of the Maester and Token Tactics V2 tools. His work focuses on Microsoft Entra and the Defender suite, helping customers secure their cloud environments.LinkedIn - https://www.linkedin.com/in/fabianbader/🔗 Related Links* Fabian’s Blog - https://cloudbrothers.info/* Entra Scopes - https://entrascopes.com/* Maester - https://maester.dev/* Token Tactics V2 - https://github.com/f-bader/TokenTacticsV2📗 Chapters 02:19 The Story of the "Cloud Brothers" Blog 03:32 The Origin Story of Maester 07:39 Token Tactics V2 & Continuous Access Evaluation 09:43 How Conditional Access Bypasses Are Found 12:05 What is FOCI (Family of Client IDs)? 18:04 Hardening Your Conditional Access Policies 29:59 V1 vs V2 Token Endpoints Explained 38:19 Using Graph Activity Logs in Defender XDR 42:45 The New Group Source of Authority (SOA) 54:59 Workplace Ninjas US AnnouncementPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple 📺 YouTube → https://entra.chat/youtube 📺 Spotify → https://entra.chat/spotify 🎧 Overcast → https://entra.chat/overcast 🎧 Pocketcast → https://entra.chat/pocketcast 🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx 👔 LinkedIn → linkedin.com/in/merill 🐤 Twitter → twitter.com/merill 🕺 TikTok → tiktok.com/@merillf 🦋 Bluesky → bsky.app/profile/merill.net 🐘 Mastodon → infosec.exchange/@merill 🧵 Threads → threads.net/@merillf 🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
In this episode, I sit down with my boss, Tarek Dawoud, to pull back the curtain on what really happens during a major service outage. Tarek shares some incredible "war stories" from his time in the trenches, from the early days of DirSync where the team had to edit a sync file with a debugger to prevent an incident, to the massive outages of 2017 and 2018 that changed everything. We'll give you a peek into the high-stakes, quick-thinking world of a "live site" incident and reveal the groundbreaking engineering principles like cell-based architecture and the backup authentication service that were born from these challenges, making Entra more resilient than ever before. Subscribe with your favorite podcast player or watch on YouTube 👇About Tarek Dawoud Tarek Dawoud is a Lead Architect in the Customer Engineering team for Microsoft Entra. With years of experience growing up in Entra engineering, he has been involved in his share of outages and has a deep understanding of what it takes to build and maintain a resilient, hyperscale identity service. LinkedIn - https://www.linkedin.com/in/tarekdawoud/🔗 Related Links * SLA performance for Microsoft Entra ID - aka.ms/entraidsla * Microsoft Blames "Severe Weather" for Azure Cloud Outage * Microsoft Probes Cause of Global Web Outage* Microsoft's Azure AD authentication outage: What went wrong📗 Chapters00:57 What is a "Live Site"? 14:15 The Secret to Entra's Uptime: Cell-Based Architecture 18:09 How Entra Routes Your Login Request Globally 24:46 War Story #1: The 2017 Conditional Access Outage 29:52 War Story #2: How a Hurricane & an Office Bug Caused Chaos 43:39 The Backup Auth Service: Entra's Secret Weapon 57:54 Does the Backup Service Kick in Automatically? 01:04:16 Regional Isolation & The Power of Managed Identity 01:08:17 Anatomy of a Near-Outage in 2021 01:12:02 How Microsoft's Culture Learns From MistakesPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
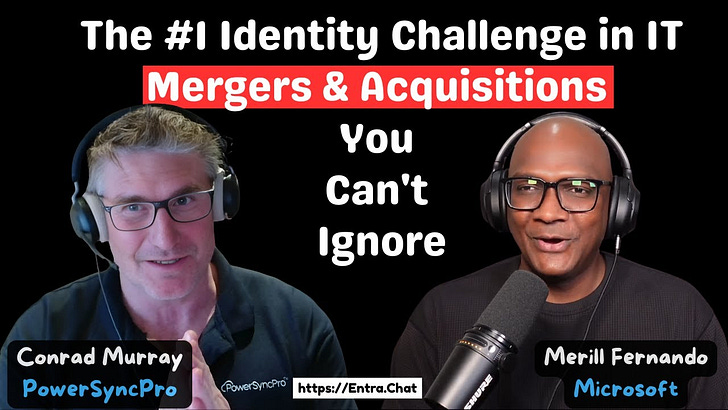
In this episode, I sit down with Conrad Murray, a seasoned expert who lives and breathes the complexities of IT migrations during mergers, acquisitions, and divestitures.We dive deep into the real-world challenges that companies face, from the political battles of deciding whose tenant to use, to the technical nightmares of migrating three-quarters of a petabyte of data for a major global firm.Conrad shares some incredible "war stories" about the single hardest part of any migration—the domain cutover—and reveals why the success of a months-long project boils down to just the first four hours of the end-user experience on a Monday morning. Subscribe with your favorite podcast player or watch on YouTube 👇About Conrad MurrayConrad Murray is an expert in the IT lifecycle, specializing in complex tenant-to-tenant migrations for mergers, acquisitions, and divestitures. With over 15 years of experience moving companies to the cloud, Conrad has seen it all, from early BPOS and Lotus Notes migrations to massive, petabyte-scale Microsoft 365 consolidations.LinkedIn - Conrad Murray🔗 Related Links* Google to Microsoft 365 Migrations* PowerSyncPro📗 Chapters00:00:00 Intro 00:05:40 The Politics of Merging Tenants 00:07:23 Greenfield Tenants: A Fresh Start 00:09:58 War Story: Migrating 750TB for S&P Global 00:19:13 The Nightmare of Domain Cutovers 00:25:14 The Critical Day-One User Experience 00:30:00 Reconfiguring Mobile Devices: The Hardest & Easiest Part 00:35:46 Multi-Tenant Orgs (MTO): A Long-Term Solution? 00:49:22 The Unique Challenges of Divestitures 00:55:17 Data Cleanup That Never Happens 01:01:06 Tools of the Trade for Migration SuccessPodcast Apps🎙️ Entra.Chat - https://entra.chat🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe
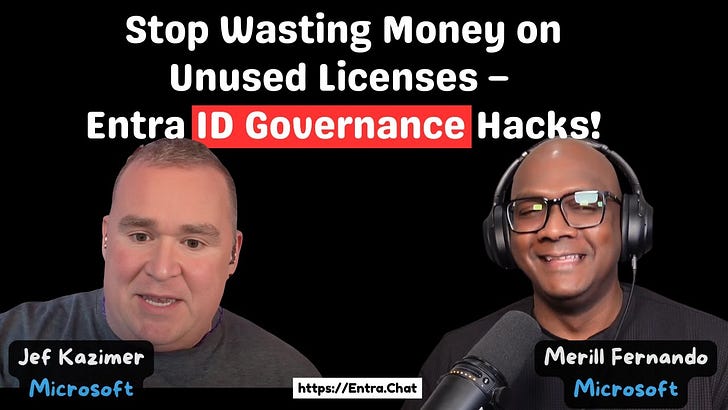
In this episode we are joined by Jef Kazimer, Principal Product Manager at Microsoft to discuss the critical role of Microsoft Entra ID Governance. We explore the entire identity lifecycle from joiners, movers, and leavers (JML), the financial and security benefits of automated provisioning, and the pitfalls of legacy IGA solutions. Jef shares his extensive experience, from deploying complex MIM solutions to helping shape the future of cloud-native governance, and provides key insights into how AI will drive the need for more robust governance and how Entra is leveraging technologies like Azure Logic Apps for supportable, long-term solutions.Subscribe with your favorite podcast player or watch on YouTube 👇About Jef KazimerJef Kazimer is a PM on the Microsoft Entra team, specializing in Identity Governance. With a career spanning from help desk support and consulting to his current role in engineering, Jef has a deep understanding of the real-world identity and access management challenges that organizations face. He is passionate about helping customers secure their environments by leveraging the power of the cloud.LinkedIn - https://www.linkedin.com/in/jefkazimer/🔗 Related Links• Entra ID Governance licensing docs - https://learn.microsoft.com/en-us/entra/id-governance/licensing-fundamentals📗 Chapters01:39 From Atari to Microsoft: A Hacker's Journey 09:14 What is Identity Governance (and Why You're Already Doing It) 13:16 The Hidden Costs of Poor Governance & Licensing 15:58 The Customization Trap: Why 'Simple' is Better 22:57 Common Challenges in Identity Governance 27:36 Governance for Small vs. Large Businesses 30:51 The Secret to Great User Experience 42:33 Demystifying Entra ID Governance Licensing 46:41 The Future: How AI Changes EverythingPodcast Apps🎧 Apple Podcast → https://entra.chat/apple📺 YouTube → https://entra.chat/youtube📺 Spotify → https://entra.chat/spotify🎧 Overcast → https://entra.chat/overcast🎧 Pocketcast → https://entra.chat/pocketcast🎧 Others → https://entra.chat/rssMerill's socials📺 YouTube → youtube.com/@merillx👔 LinkedIn → linkedin.com/in/merill🐤 Twitter → twitter.com/merill🕺 TikTok → tiktok.com/@merillf🦋 Bluesky → bsky.app/profile/merill.net🐘 Mastodon → infosec.exchange/@merill🧵 Threads → threads.net/@merillf🤖 GitHub → github.com/merill Get full access to Entra.News - Your weekly dose of Microsoft Entra at entra.news/subscribe